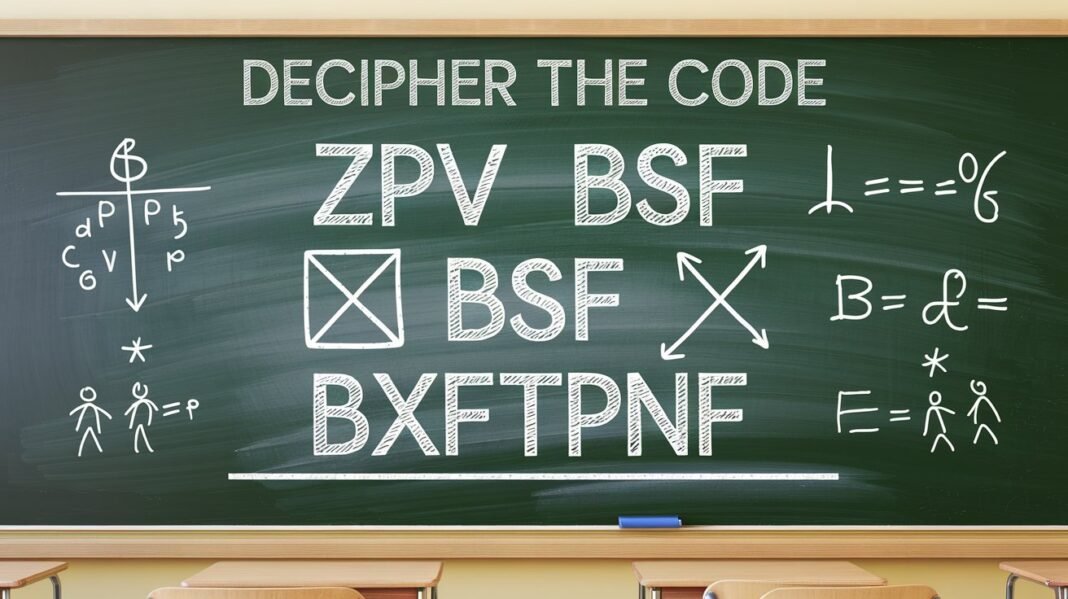
Have you discovered an elusive statement that needed your attention because you could not understand its hidden message? Please greet “Decipher the Code ZPV BSF BXFTPNF,” which might contain valuable information but looks totally nonsensical. For centuries, people have been fascinated by codes and ciphers, and this enigma presents us with an opportunity to learn about decoding techniques. Our research will show what this enigmatic text represents and reveal how other coded puzzles evolved into powerful forces that influenced historical changes. Experience an exciting exploration of hidden messages that will both educate and entertain you, whether you already love mystery solving or want to try decoding codes. Get ready to solve this mystery.
Introduction to Codes and Ciphers
For centuries, codes and ciphers have captured the imagination of people across the globe. They depict the existence of a realm that is filled with secrecy, hidden meanings, and intrigue that are just waiting to be uncovered. The practice of encoding messages has always been a vital form of communication throughout the ancient scrolls era as well as in modern-day spying.
What do you think “Decipher the Code ZPV BSF BXFTPNF” stands for? Initially, it might seem like utter absurdity, yet beneath its surface is the potential for something beyond one’s own self. Are you prepared to go on a journey filled with a world of codes? Let’s delve further into the topic’s profound roots alongside attempting to solve this unique enigma together!
History of Secret Codes
For centuries, secret codes have piqued the interest of mankind. In their most primal form, they were utilized for communication in warfare and diplomatic affairs in ancient civilizations. The Greeks applied simple combinations while the Romans made use of the well-known Caesar cipher.
With the passage of time, coding techniques evolved. During the Middle Ages, monks sought refuge in creating complex ciphers to shield religious scripture from the outside world. This formed the basis of more elaborate systems to come.
In the 20th century, the world witnessed tremendous innovation with the inception of the Enigma machine during World War II. This device significantly changed the course of events by encrypting and decrypting crucial military communications. This machine played a crucial role in demonstrating the importance of secure communication in times of chaos.
This legacy continues in the modern world, where protecting one’s online identity is becoming increasingly essential due to the current digital nature of the world. It’s safe to argue codes are more than simple relics; they are a necessity that evolves parallel to technology and the needs of mankind.
Modern-Day Uses of Codes
In today’s internet-driven world, codes are ubiquitous. Encryption conceals the contents of our texts and emails, while professional coding techniques are necessary for businesses to access sensitive data.
Social media channels are inundated with code that serves the dual purpose of aiding in the screening of information such as spam and tailoring content to each user. Algorithms utilize coded languages to detect and track data trends, enhancing security.
In gaming, codes are more often associated with cheats or unlocking advancement levels, features, props, and skins. Communities of avid gamers ignite excitement and competitiveness as they share these secrets.
Moreover, artists apply codes to their work to give it a modern expression. Incorporating hidden meanings makes art more appealing because viewers are more keen on decoding them.
In finance, it has become commonplace to utilize cryptographic techniques to strengthen online transactions, adding additional safety to banking features. Placing trust in these techniques leaves support clauses in place that protect against danger as these tricks become more intricate.
With the improvement of technology comes the innovation of coding systems that are more efficient. As such, the provision of accessibility to single codes within so many domains remains challenging. The need to comprehend codes is still relevant in modern society today.
Breaking Down: Decipher the Code ZPV BSF BXFTPNF
The expression ZPV BSF BXFTPNF will appeal to anyone familiar with ciphers. Upon first glance, it seems like a jumble of characters, but there is something underneath. This format resembles a very simplistic Caesar cipher that is straightforward to decode. This encryption method applies a shift to each letter down the alphabet.
If we shift “ZPV” one down, “YOU” is the result. Following this pattern further reveals the entire phrase to be “YOU ARE AWESOME.”
ZPV ZBSF YBFTPNF can serve as playful notes amongst friends or as unique affirmations. Isn’t that what decoding is all about? Not only do secrets exist, but innovative methods can unlock a multitude of positive energies.
Employing such ways of verse cracking aids in sharpening one’s wits and encouraging them to think creatively, which is of immense importance to more than just being able to crack codes.
Explanation of the Code Format
The phrase ‘ZPV BSF BXFTPNF’ appears to employ a common form of encryption referred to as the Caesar cipher. This entails shifting every letter in the original message by a predetermined number of letters either up or down in the alphabet.
In this instance, the shift is one letter to the left. In other words, ‘Z’ becomes ‘Y’, ‘P’ changes to ‘O’, etc. The same holds for the other words.
This particular approach makes it simple to code but still fun to work with. The difficulty comes from knowing what the pattern is rather than needing to work out complicated symbols or algorithms.
Recognizing such styles of ciphers is crucial for the decryption of messages in a timely manner. Basic knowledge of ciphers gives an opportunity to a person interested in cryptography to delve deeper without hesitation and deal with complicated encryption confidently.
Possible meanings and interpretations
The challenge of cracking the code is that ‘ZPV BSF BXFTPNF’ presents a potential world of meaning. On the surface, one could interpret this phrase as a meaningless combination of letters. But herein lies the appeal.
One of the possible explanations could be letter shifting alphabetically. When one applies a simple Caesar cipher, there is a shift of one place backwards for each letter. Strikingly, ‘ZPV’ goes to ‘YOU,’ and ‘BSF’ goes to ‘ARE.’. What lies at the surface of the message is engaging. The use of ciphers reveals the appeal of the layered structures that tell the story.
Another view to consider is that this term is part of some insider or group slang language. These codes serve as a form of friendly banter among friends or in organizations where maintaining confidentiality is crucial. Each perspective is a reflection of creativity and its context, which gives joy in understanding what is behind each coded phrase and how meaning shifts through attention.
How to Solve the Code
To decipher the message, “You are a secret,” start by evaluating the code structure and patterns within the text. Start by guessing the techniques used for setting the code, such as stray words or known phrases that come to mind. If there’s no head start available, then conventional techniques like the Caesar method can be employed, where the letters used are shifted a few spaces ahead in the alphabet set.
Second, these coded messages need to be carefully analyzed. For example, a one-step backward shift can be used to see letters like Z turning into Y or P turning into O. Each shift shows the position of the previous letter. This type of backwardness provides a subtle yet consistent methodology rather than the brute force approach of guessing every range.
After the process of separating words and hoping for alignment to the guide comes, putting every outcome resulting from the educated guess diolitics together helps make sense of the earrings that the idea of familiar phrases abound.
Once the phrases are deciphered and put together, keeping track of the spaces between the letters can reveal the true hidden beauty in the letters’ combination.
This rudimentary level of thinking can be useful when the hidden code consists of missing combinations of phrases or structure.
In this case, document all relevant details and the surrounding environment to gain a clear understanding of why C has an advantage. To gain a deeper understanding, it is necessary to break down codes, a process that requires both creative thinking and ingenuity.
Famous examples of coded messages
Numerous instances of coded messages have captivated the world throughout its history, the most notable being the usage of the Enigma machine during the Second World War. This advanced technology enabled German forces to code their messages, thus preventing their Allies from easily deciphering them. As a result, it was next to impossible for Allied decipherers to interpret German communication.
Another fascinating example that comes to mind is the modern-day treasure hunting competitions. In these competitions, participants must first solve intricate puzzles and cryptographic challenges to uncover the hidden treasure. These challenges generally consist of elaborate codes and riddles, fostering a daredevil spirit among the participants.
Let us not forget the case of the Zodiac Killer ciphers from the late 1960s, where the infamous Zodiac Killer sent multiple letters to jeer at the authorities, some of which were never solved for decades until cracked by modern-day amateur detectives.
It becomes evident how these examples portray the information setting, as they highlight how codes serve not merely as secrecy but as puzzles that pique curiosity, the majority of the time necessitating cross-collaborative efforts.
Enigma Machine in WWII
The Enigma machine was a groundbreaking technology that played a key role in the Second World War. Originating in Germany, it facilitated encrypting sensitive military information through a cryptic system of rotors and wires, which enhanced the level of confidentiality of the deep state communication between the top generals.
One of the most powerful aspects of the machine was the changing ciphers. Each and every piece of information could have different codes to censor everything, which made interception almost futile. This single attribute made it crucial for the Allies to break the code, as each reconstructed message could potentially alter the entire scope of the battle.
Alan Turing, capitalizing on the centuries of mathematics, helped break the military code of the Germans, which made him one of the most revered Englishmen of Bletchley Park, who, apart from him, had a plethora of other mathematicians employed to crack the paradoxical secrets hidden deep within the Enigma.
The powerful decryption provided countries with critical intelligence that assisted in stopping the German plan to have millions of casualties. The importance of codebreaking and technological development during such high-tension global times became clearer as time progressed.
Cryptographic Puzzles in Treasure Hunts
One of the newest features of modern treasure hunting is the use of cryptographic puzzles. It enhances the experience for treasure hunters, as they have to use their investigative skills.
While attempting to find the next clue or location, participants have to solve codes. This can take them through parks and obscure parts of their neighborhoods or even entire cities.
The complexity of these puzzles can range from simple ciphers, such as Caesar shifts, to advanced ones with various layers of encryption. Each twist presents difficulties that keep these hunters guessing.
In addition, many treasure hunts include historical references that help blend entertainment with education. This includes not only deductive reasoning but also knowledge of the history of cryptography, which enriches the participant’s intellectual arsenal.
That feeling of working toward a different end goal and solving an enigma is very deep and resonates strongly with puzzle enthusiasts. With every message deciphered, feeling excited and accomplished for what lies ahead is inevitable.
The importance of code-breaking skills
Understanding the context of these words in a sentence proves fundamental reasoning in a digital era. Understanding how to interpret messages has become increasingly important, particularly with the rise of cyber terrorism.
These skills are required for cracking codes and even for certain gaming activities. They assist in national defense as well as personal privacy.
This translates into code breaking, provoking more critical thinking and problem-solving. This skill encourages self-exploration and enables a person to look at problems from multiple dimensions and angles.
Puzzles in the form of ciphers can lead to thrilling job prospects in new-age domains such as cybersecurity, intelligence agencies, defense, and engineering. People who are skilled in these domains are extremely useful in protecting and gathering sensitive information.
People who decipher messages can have their interests triggered in the history of technology. Every message encoded holds a chain of events that brought about the need for such codified information due to the multitude of lies hidden within history.
These are only a few of the advantages people globally could employ if they decided to learn binary codes.
Final Thoughts
Expecting to receive a burden that dramatically changes how people perceive you can be quite daunting. In the background information, there is an analysis of the factors that encourage liars and forgery, which has become more common and uses advanced technology to make the harm and suffering it causes even worse.
With that said, being unable to make sense of the intricate codes (ZPV BSF BXFTPNF, for example) can be just as problematic. Skills like these can amplify one’s appreciation for history and technology, all the while having the ability to empower individuals, be they hobbyists or professionals in fields such as cybersecurity, espionage, or solving puzzles, and so forth.
Previously: Touchless Car Wash